File a Report
Find out how to report and respond to many types of security concerns.
Report a Lost or Stolen Item
If your electronic device (including laptop, cellphone, or tablet) has been lost or stolen, please contact the Stevens Police Department at (201) 216-5105 and file a police report.
Additionally, please contact the Office of Information Security at security@stevens.edu to evaluate if protected data was present on the device, including but not limited to:
- Health records
- Employee/personnel records
- Student data
- Research data
- Financial records
Report a Security Vulnerability
If you have discovered or suspect a security vulnerability on any systems owned or operated by Stevens Institute of Technology, please report it immediately:
Report the vulnerability to the Information Security Office by emailing security@stevens.edu Please provide as much information as possible. Never include sensitive information over email, instead, call us at 201-380-6599.
Include in your report:
- Your name and contact information
- Which systems are affected (IP addresses, hostnames, URLs, etc.)
- Description of the security vulnerability and steps to reproduce the issue
- Date and time the vulnerability was discovered
- Any other known resources affected.
What is a Security Incident?
A security incident is any attempted or actual unauthorized access, use, disclosure, modification, or destruction of information. This includes interference with information technology operations and violation of campus policy, laws, or regulations. Examples of security incidents include:
- Computer system breach
- Unauthorized access to, or use of, systems, software, or data
- Unauthorized changes to systems, software, or data
- Loss or theft of equipment used to store institutional data
- Denial of service attack
- Interference with the intended use of IT resources
- Compromised user accounts
Actual or suspected security incidents must be reported as early as possible so that campus can limit the damage and cost of recovery. Include specific details regarding the system breach, vulnerability, or compromise of your computer and we will respond with a plan for further containment and mitigation.
How to report a security incident email: security@stevens.edu
Important: If the incident poses an immediate danger, contact Campus Police immediately at (201) 216-5105 or call 911. Information to include in the report:
- Your name
- Department Email address
- Telephone number
- Description of the information security problem
- Date and time the problem was first noticed (if possible) Any other known resources affected
What should I do if I suspect a serious security incident?
A security incident is considered serious if the campus is impacted by one or more of the following:
- potential unauthorized disclosure of sensitive information
- serious legal consequences severe disruption to critical services
- active threats are likely to raise public interest
Sensitive information is defined in the Data Classification Standard and includes personally identifiable information that is protected by laws and regulations, as well as confidential research protected by data use agreements, such as:
- Social security number
- Credit card number
- Driver's license number
- Student records
- Protected health information (PHI)
If you know or suspect that the compromised system contains sensitive data, please take these steps:
- Do not attempt to investigate or remediate the compromise on your own
- Instruct any users to stop working on the system immediately
- Do not power down the machine
- Remove the system from the network by unplugging the network cable or disconnecting from the wireless network
- Report the incident using the instructions above
In the case of a serious incident, please be aware that continued interaction with a compromised machine can severely affect the forensic analysis.
Report Computer or Network Misuse
A security incident may also refer to the inappropriate use of computers and the campus network. Common violations and examples of misuse include:
- Communications for commercial or political marketing purposes
- Email spam
- Copyright infringement allegations
If the misuse in question originated from a campus email address, network connection, or resides on a Stevens website, email: security@stevens.edu.
Otherwise, complaints must be directed to the off-campus service provider. You may use the Abuse.net tools to look up the appropriate service provider:
- Abuse.net: Lookup abuse contact for a domain
- Abuse.net: Send a complaint to the off-campus service provider For information about how to respond to online copyright infringement allegations, see the following list of resources: The Digital Millennium Copyright ACT (DMCA) and Related Resources
Report a Phishing Email
Although your first instinct may be to ignore or delete suspicious emails, we recommend that you report them to our security team. We will examine the email and advise you of any further steps you may need to take.
New Method to Report Phishing Emails
The "Report Phishing" button is a new feature in Outlook that will help users immediately report phishing emails to the Office of Information Security.
This button provides a simple method for users to report suspicious emails such as spam, phishing, and other malicious content. To do so, highlight the message in question and click on the Report Message button in the Outlook ribbon. This will move the email from your Inbox to your Junk Email folder and send a copy of the email to the Office of Information Security team for evaluation.
If the Report Phishing button is not available, you can forward the email as an attachment to security@stevens.edu.
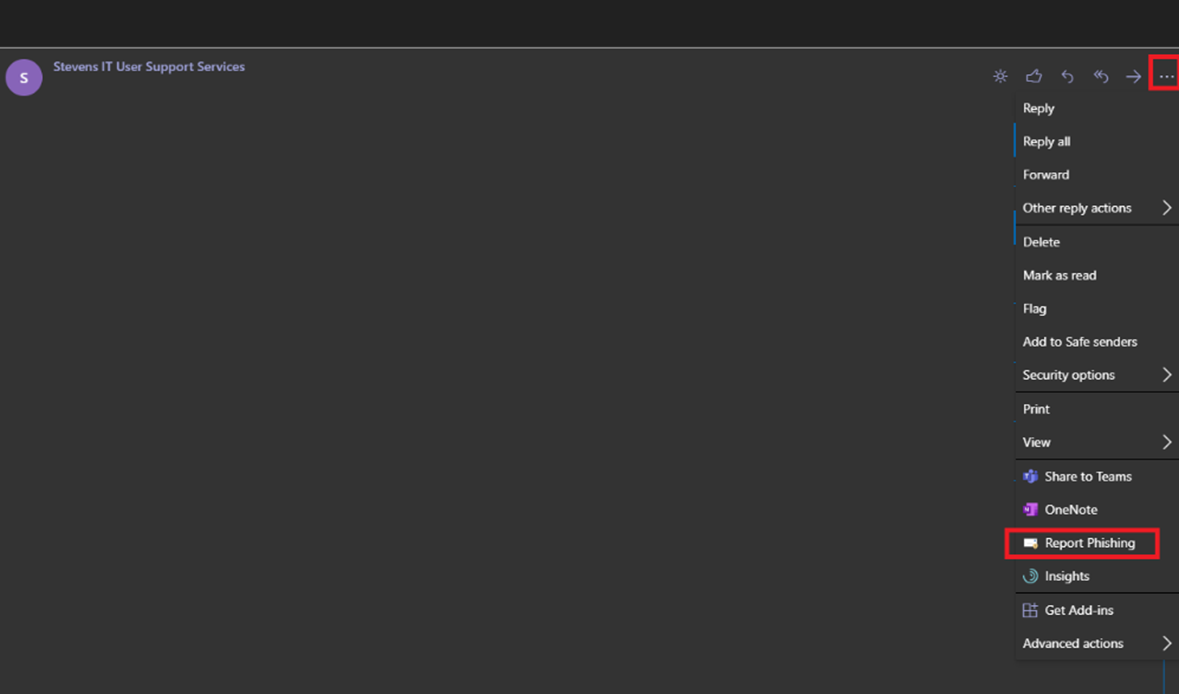
Step 1: Click on the email that you would like to Mark as Phishing.
Step 2: Click the Ellipses.
Step 3: Click Report Phishing.
Report Abuse
If you suspect that your network, systems, or services may have been negatively impacted by resources at Stevens, please report them to the Office of Information Security via email to: security@stevens.edu.
When reporting abuse, provide the following:
- Your name, and an email address or phone number for contacting you
- If you are affiliated with Stevens, your affiliation (Faculty, Staff, Student, etc.)
- The type of abuse (SPAM, bandwidth abuse, etc.)
- The IP address of the attacking system, if appropriate
- The date and time of the abuse
- Any additional information that you feel may help us to locate and diagnose the problem, such as full message headers, system logs, etc.
Experiencing an issue or need additional support, contact our OneIT Team by